Active Directory Protection from Advanced Cyberattacks:
Defend Your Business from Active Directory Attacks with Certes Data Protection and Risk Mitigation
Active Directory (AD) plays a critical role in your organization, managing user authentication, authorization, and security across your entire IT infrastructure. However, this essential system has become a high-priority target for cybercriminals, with advanced attacks like Volt Typhoon demonstrating the catastrophic potential of compromised AD environments.
Whether you’re facing threats from nation-state actors, ransomware gangs, or internal vulnerabilities, Data Protection and Risk Mitigation is paramount to ensuring your business stays safe. Certes delivers state-of-the-art solutions specifically designed to secure your AD against the most sophisticated attacks.
Such ransomware attacks have a distinct pattern and typically follows the seven stage “Kill Chain”:
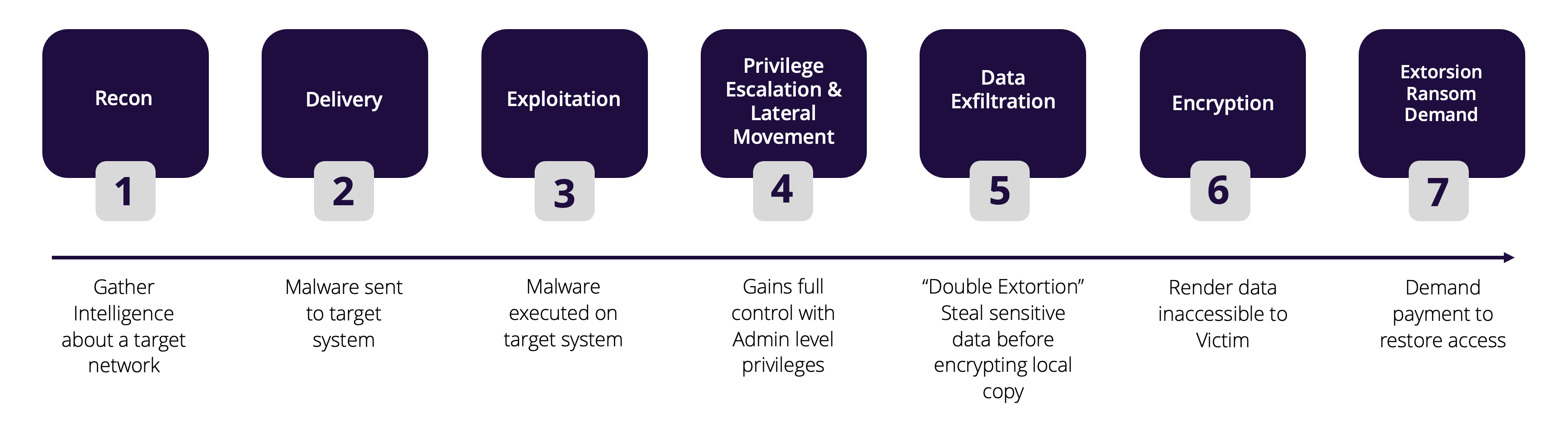
Why is Active Directory a Prime Target for Cyberattacks?
Attackers focus on Active Directory because it controls access to your most sensitive data. Once infiltrated, attackers can escalate privileges, move laterally, and even take control of the entire network. With the increasing complexity of IT environments—especially as more organizations embrace cloud services and remote work—the risk of AD breaches has never been higher.
The Volt Typhoon attack underscored the importance of strengthening AD protection, as attackers can infiltrate networks and remain undetected for extended periods. Certes’ Data Protection and Risk Mitigation takes a proactive approach by assuming breaches are inevitable. Rather than simply detecting and responding to threats, Certes ensures that even if attackers penetrate your defenses, the data they seek becomes useless, rendering the attack futile and protecting your organization from meaningful harm.
From ransomware to espionage, Active Directory attacks are on the rise. Traditional security tools often fail to detect modern threats, especially as attackers exploit these legitimate administration tools, in a technique known as Living Off the Land (LOTL), leaving your AD environment vulnerable to stealthy compromises. Attacks can go undetected for months, causing irreparable damage to your organization.
Data Protection and Risk Mitigation is critical for defending against Active Directory attacks; 100% data focused, Crypto Agile and Quantum Safe and has never been hacked. Our state-of-the-art DPRM solution acts as a formidable defense against the rising threats of data breaches and ransomware attacks, ensuring a solid foundation for your digital assets, and breaking the ransomware kill chain before attacks can escalate.
Free Whitepaper Download - Active Directory: Breaking the Kill Chain
Download the whitepaper to discover:
• The latest trends in Active Directory-targeted cyberattacks
• The true cost of a breach vs the cost of prevention
• Best practices for securing your AD infrastructure
• How Certes AI’s Data Protection and Risk Mitigation can defend your business
Certes Strengthens Global Security Landscape Through Strategic Partnership with DeployPartners

Certes is advancing its mission to deliver quantum-ready data protection by forming a strategic partnership with DeployPartners, a recognized leader in operations, security, and cloud optimization. This collaboration brings together two highly specialized organizations with complementary strengths, creating a new level of capability for enterprises seeking stronger, more resilient security architectures.
It’s the Most Wonderful Time of the Year… Unless You’re Hit by Ransomware

Hospitals across the US rely on legacy infrastructure that was never built to meet today’s cybersecurity demands. MRI scanners, patient monitors, and lab systems often run on outdated operating systems. Replacing them is challenging and costly. Many of these machines are FDA-certified, and any software change can trigger a recertification process, leading to costly downtime.
NYDFS Expects End-to-End Control of Sensitive Data. Can You Prove It?

Hospitals across the US rely on legacy infrastructure that was never built to meet today’s cybersecurity demands. MRI scanners, patient monitors, and lab systems often run on outdated operating systems. Replacing them is challenging and costly. Many of these machines are FDA-certified, and any software change can trigger a recertification process, leading to costly downtime.
Request a Callback
Ready to see Certes in action? Book a call with us today.
Active Directory breaches can lead to significant business losses, both financially and reputationally. Don’t leave your AD infrastructure exposed. Download our free white paper now to understand the full scope of the threats and learn how Certes AI’s Data Protection and Risk Mitigation solution can safeguard your business.
Take action to secure your company against cyber threats and compliance challenges and request a callback with Certes today. We’ll ensure your data remains secure, accessible and the essential service you deliver to customers is uninterrupted.




