It’s all about the data.
Regulators focus on it, cyber criminals want it, and CISOs and compliance officers are caught in the middle, worrying how to protect it in the wake of ever-increasing constraints on people and budgets.
Notwithstanding today’s risk and threats from bad actors, another challenge looming on the horizon is the threat posed by quantum computing, which is discussed at this link.
The problem gets worse because current security capabilities that build higher walls around enterprise networks only detect threat events that have already occurred. Stealthy cyber criminals still manage to get inside networks, where they perform reconnaissance, spread laterally and exfiltrate data with impunity.
Certes provides Quantum Safe Data Protection and Risk Mitigation (DPRM) capabilities to businesses, governments and other organisations that are concerned about protecting critical data. DPRM proactively safeguards before cybercriminals damage and exfiltrate data during backups, on servers and while in transit.
The term end-to-end encryption is frequently used in cybersecurity, but it can fall short of its promise. Many solutions only encrypt data between specific nodes or within segmented parts of the network, leaving points of exposure where data is briefly decrypted for inspection, routing or policy enforcement.
Certes takes a fundamentally different approach. Its architecture enforces persistent encryption so that data remains protected from its point of origin to its destination. Data is not exposed in plaintext, even during transit across internal networks or third-party infrastructure. This targets common vulnerabilities introduced by intermediate decryption and significantly reduces the attack surface.
This is more than encryption. It’s data-in-motion security as it was originally intended – continuous, verifiable and resistant to compromise.
The Certes model delivers:
▪ Quantum-Safe Protection – Post-quantum cryptography is built into the data layer, not bolted on later.
▪ Regulatory Readiness – Supports GDPR, DORA, NIS2, and CJIS compliance with enforced key ownership and audit-friendly controls.
▪ Zero Trust Enablement – No trust in the network, full trust in the data.
▪ Operational Longevity – Future-proofs sensitive data so it’s not exposed years from now when legacy encryption is forecast to collapse.
Certes Enforcement Points (CEP) implement the DPRM controls and can be deployed as bump-in-the-wire devices, virtual CEPs (vCEPs) and containers or in the cloud (cCEP). It all depends on how close a customer wants to put the protection to the applications.
As more organizations seek to implement workloads across datacenters, public cloud and edge compute facilities, they are naturally turning to vendors that offer seamless and comprehensive capabilities to manage across such environments.
Nutanix delivers hybrid and multicloud infrastructure that enables IT to run apps and data anywhere. The Nutanix Cloud Platform (NCP) solution natively converges silos of compute, storage, networking, and virtualization in a hyperconverged platform to run workloads at scale.
Through the Nutanix Prism hybrid multicloud management system, IT organizations can accelerate application infrastructure deployments and simplify operational management through one-click provisioning capabilities. Prism centralized management and orchestration automates configuration, provides essential analytics capabilities and does not require separate infrastructure.
The Nutanix AHV hypervisor extends advanced virtualization capabilities to modern hybrid and multicloud environments. Featuring a distributed systems core designed for the cloud, Nutanix AHV is designed to solve today’s complex enterprise IT challenges.
The Certes vCEP is validated by Nutanix to run on Nutanix AHV to power VMs and containers on-premises and in public clouds. The Nutanix Ready – AHV badge is awarded to products and solutions that have been tested and verified to work with Nutanix AHV. The Nutanix compatibility and interoperability matrix shows which version combinations have been validated.
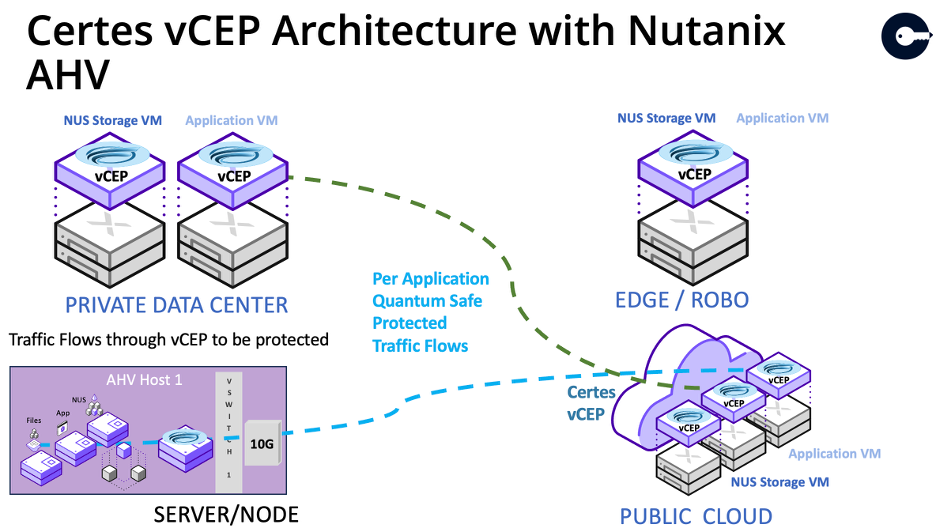
By sitting on the Nutanix AHV hypervisor, the DPRM capabilities can be easily configured between the physical ports of a node and the VMs running there, which pushes data protection capabilities as close to the source of data as possible.
The benefits of this are:
1) Data is protected in VMs before leaving a physical port, making reconnaissance, lateral movement and exfiltration attempts by threat actors a fruitless endeavour.
2) Simplicity of deployment with control of the policy and keys kept in the hands of the data protection team. A vCEP is a bump in the wire that resides on the node, so network implementation and design processes need not be engaged.
3) Quantum safe protection for every VM mitigates the risks associated with legacy protocols, encryption capabilities and breaches due to exfiltration of data from VMs.
This allows organizations to rapidly and easily address the top-of-mind issues that CISOs are thinking about.
▪ Deploying a global quantum safe strategy.
▪ Protecting cyber vault backup and recovery systems to help ensure data integrity.
▪ Stopping the ransomware kill chain on Active Directory on Nutanix AHV by preventing the exfiltration of data by cyber criminals.
▪ Protecting critical AI data traffic and assets from poisoning, exfiltration and damage when building AI infrastructures.
Implementing Certes Quantum Safe DPRM vCEPs on Nutanix AHV gives organizations the ability to build scalable, simple and comprehensive data protection capabilities into their nodes to reduce the risks that CISOs, compliance officers and executives are concerned about.
Contact Certes to find out more.

